Residential Proxy Detection
Fraudsters and Attackers evade website protections by proxying through residential proxies. Turn their biggest weapon against them.
Determine with unparalleled accuracy and zero latency whether a request was made through a proxy, on a per-request basis.
0ms
Latency
Residential Proxy networks are used by fraudsters to anonymise their true address while avoiding known VPNs. Use the fact a request is coming from a proxy as a signal to combat fraud.
99%
Reduction in fraud
Residential proxies are a major selling point of the multitude of SaaS web scraping services promising to evade website protections.
280k
Brightdata Australian Residential IPs
Block Scraping Services
100%
Block BrightData
100%
Block ZenRows
100%
Block ScraPoxy
Why Choose Our Residential Proxy Detection
Our solution offers unparalleled accuracy and performance.
Accurate Detection
Identify proxy usage with high precision.
Zero Latency
No impact on user experience.
Scalable
Handles large volumes of traffic effortlessly.
Easy Integration
Seamlessly integrates with your existing systems.
How It Works
Proxy usage is easy to control with firewall rules
-
Determine whether a request was made through a proxy, on a per-request basis.
-
Use as signal to combat fraud.
-
Block or challenge traffic
-
Log for your risk analysis
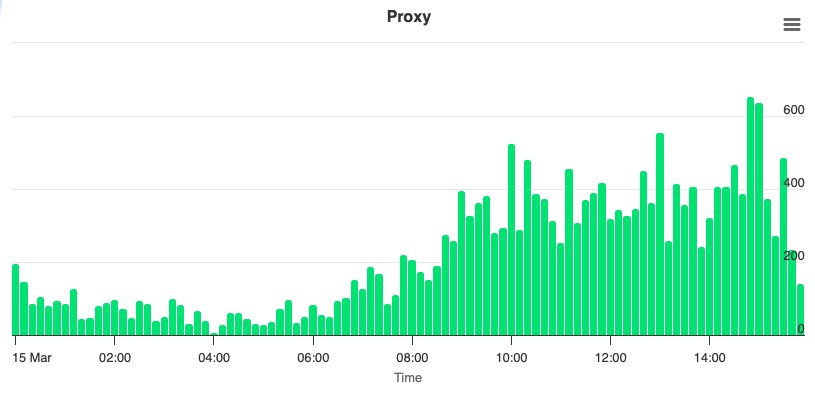
Stop Persistent Threats
Use Cases
- Prevent fraud by identifying and blocking requests from residential proxies.
- Stop credential stuffing and single hit attacks on login pages and APIs.
- Protect both APIs and Websites
- Enhance bot protection by detecting and challenging requests from proxy networks.
- Improve security decision making by using proxy detection as a signal in your systems.
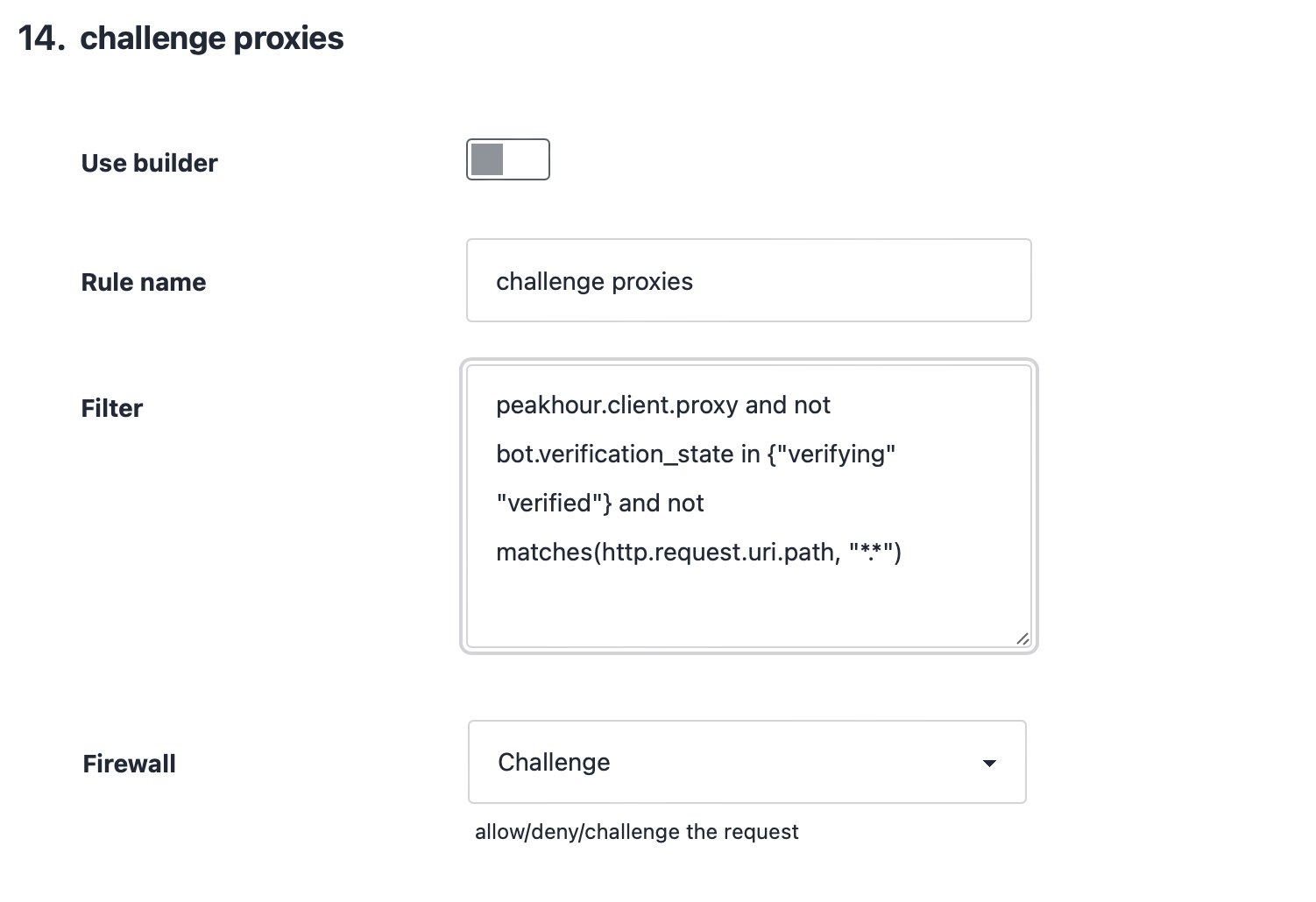
Revolutionise your fraud protection

Relevant information from our blog

Residential Proxies, Friend or Foe?
This article explores the world of residential proxies, revealing the challenges and ethical questions they pose in our GeoIP-dependent digital landscape.
Read More
The Rise of the Dragon
Residential proxy malware, and its implications for traditional cybersecurity measures, emphasising the need for evolving threat detection and mitigation strategies.
Read More
Residential Proxies and MITRE Framework: A Comprehensive Analysis
This article delves into residential proxies within the context of the MITRE ATT&CK; framework, highlighting the security implications and ethical considerations.
Read More