IP Threat Intelligence
Enhance your security posture with our advanced threat intelligence, providing real-time data on malicious IPs to proactively defend your network.
Get ProtectedThe Challenge of Identifying Malicious IPs
Attackers constantly change IP addresses and use various techniques to hide their identity, making it difficult to distinguish between legitimate users and threats. Relying on simple IP blocking is no longer enough.
Dynamic & Evasive Threats
Attackers use botnets, proxies, and TOR to constantly rotate IPs, evading static blocklists.
Data Overload
Sifting through massive amounts of traffic data to identify malicious patterns is a significant challenge.
Delayed Response
By the time a malicious IP is identified and blocked, the attack may have already succeeded.
Proactive Defence with Real-Time Intelligence
Peakhour's IP Intelligence solution provides a continuously updated database of malicious IPs, categorised by threat type. This allows you to proactively block threats and create granular security rules.
-
Global Threat Database
Leverage our vast, real-time database of over 900 million tracked IPs across 22+ threat categories.
-
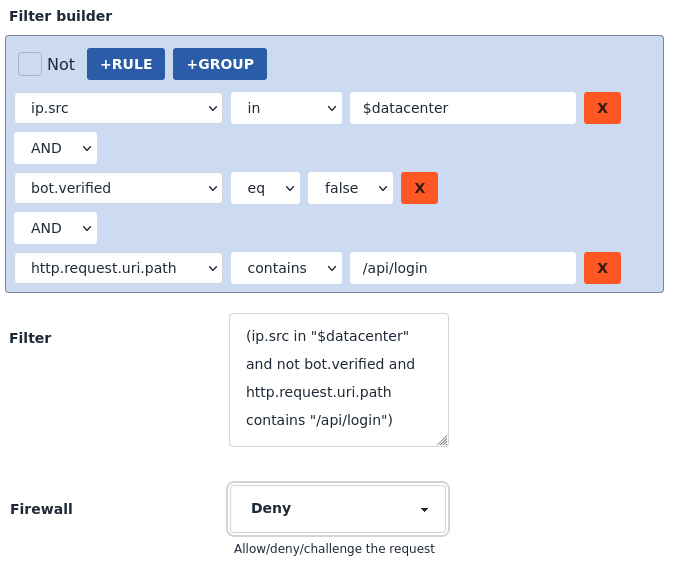
Customisable Control
Use our threat categories to create precise firewall rules. Block traffic outright or combine with other signals for nuanced control.
-
Actionable Insights
Analyse IP interaction data to make informed decisions and continually enhance your security strategy.
Enhance Your Network Security Today
Relevant information from our blog

IP Threat Intelligence
Discover and block threats through data enrichment using managed IP reputation lists
Read More
An Overview of JA4+ Network Fingerprinting and Its Implications
An in-depth exploration of the JA4+ network fingerprinting method, its applications, and its role in cybersecurity.
Read More
A Risk Based Approach To Vulnerability Scoring
An in-depth exploration of EPSS, its data-driven approach to assessing cybersecurity threats, and how it complements CVSS.
Read More