The Exploit Prediction Scoring System (EPSS) is a robust tool reshaping how we handle cybersecurity threats. Its strength lies in the diverse data sources it integrates, providing a comprehensive view of vulnerabilities. Let’s explore these components:
Data Sources of EPSS
- MITRE’s CVE List: EPSS scores only those vulnerabilities that are "published" on this list.
- Text-based “Tags”: These are extracted from CVE descriptions and related discussions.
- Publication Duration: The time period since the CVE was published.
- Reference Count: Number of references in the CVE entry.
- Published Exploit Code: Includes code from platforms like Metasploit, ExploitDB, or GitHub.
- Security Scanners: Data from security tools like Jaeles and Nuclei.
- CVSS v3 Vectors: Based on the base score in the National Vulnerability Database (NVD).
- CPE (vendor) Information: Details about the vendors of the products involved, also from NVD.
- Ground Truth Data: Real-world exploitation data from sources such as AlienVault.
EPSS Model and Tools
The current EPSS model, version 2022.01.01, employs a sophisticated methodology. It uses 1,164 variables and is based on Gradient Boosting, a machine learning technique. For a visual and interactive exploration of EPSS scores, the EPSScall tool is invaluable. It provides historical data and graphs, enhancing understanding and analysis.
The Drivers of EPSS Scores
A key to understanding EPSS is knowing what influences the scores the most. A look at the variable importance graph provides insights. It highlights the most significant contributors to the EPSS score.
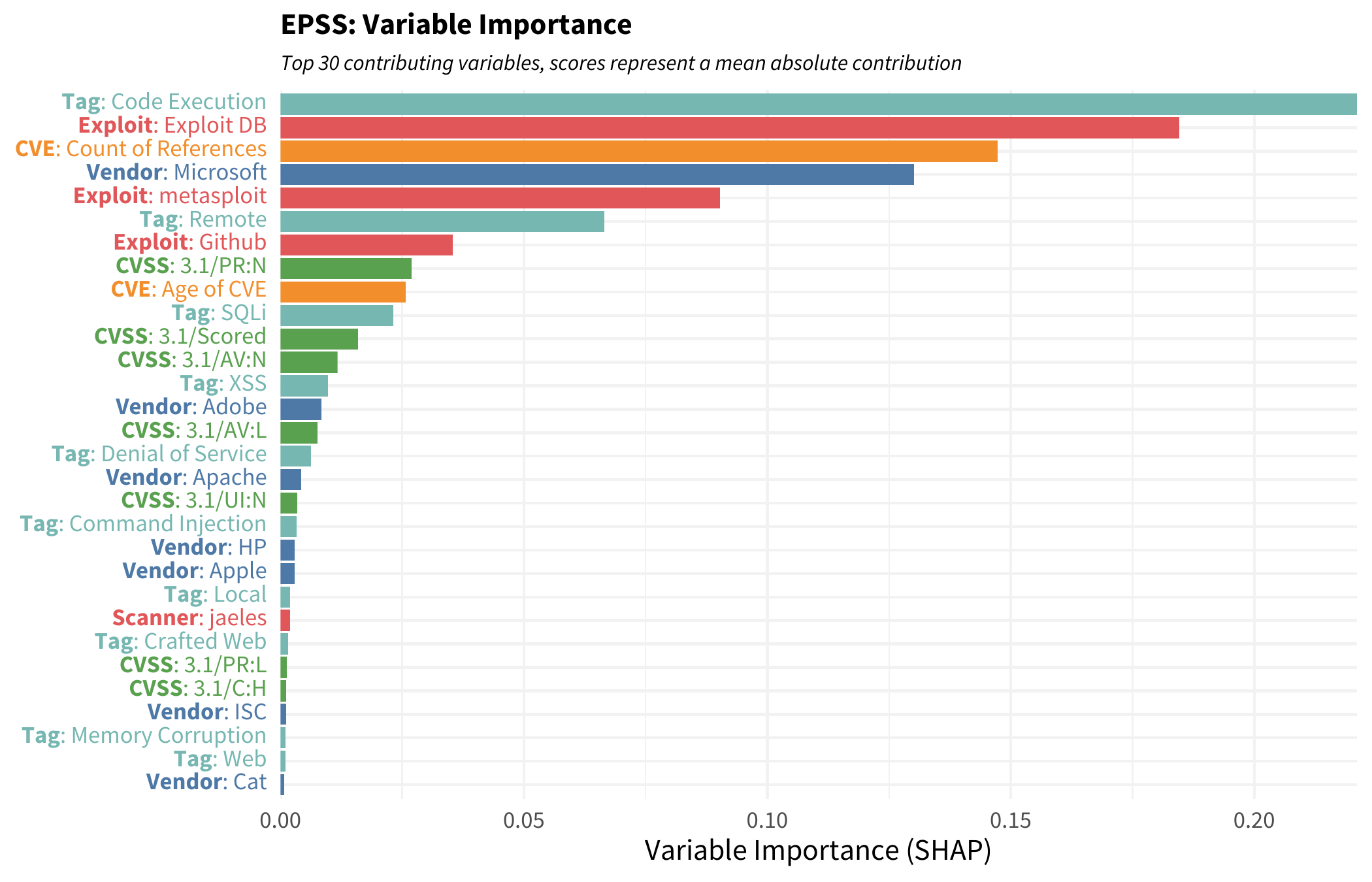
Notice how vendor data plays an outsized role in the scoring process. This graph illustrates the weight each component has in determining the likelihood of a vulnerability being exploited.
Why Does This Matter?
EPSS’s diverse data sources enable it to provide a more accurate prediction of exploit likelihood than traditional methods. By considering a variety of factors – from the age of the CVE to real-world exploit instances – EPSS gives a multidimensional view of the threat landscape. This allows network defenders to make more informed decisions about where to allocate their resources for maximum impact.
Understanding the components of EPSS also helps in appreciating its complexity and accuracy. Knowing that it's not just a single metric but a blend of various data points adds credibility to its predictions. Moreover, tools like EPSScall make these insights accessible, allowing for better vulnerability management strategies.
Final Thoughts
EPSS is more than just a scoring system; it's a comprehensive approach to understanding and managing cybersecurity threats. Its use of diverse data sources, combined with advanced machine learning techniques, makes it a critical tool for network defenders. By prioritizing vulnerabilities based on their exploit likelihood, EPSS not only enhances cybersecurity but also optimizes the use of resources in defending against cyber threats. As cyber threats evolve, so does the need for sophisticated tools like EPSS, making it an indispensable ally in the world of cybersecurity.