
The BOTS Act and the War on Ticket Scalping
A deep dive into the BOTS Act, how it's being used to investigate Ticketmaster, and the ongoing battle against ticket scalping bots.

A deep dive into the BOTS Act, how it's being used to investigate Ticketmaster, and the ongoing battle against ticket scalping bots.

Understand the shift from scripted bots to reasoning AI agents and how to adapt your security strategy for this new reality.
A deep dive into how credential stuffing attacks work, the tools used, and how to build a multi-layered defense.

Discover why traditional IP-based rate limiting is obsolete and how advanced techniques provide robust protection against modern distributed attacks.

Learn how attackers combine residential proxies and anti-detect browsers to evade detection and how modern security tools can fight back.

Explore why traditional CAPTCHAs are failing both users and security, and discover modern, invisible alternatives.

With nearly half of all internet traffic being automated, a robust bot management strategy is essential. This article explores the key considerations for effective bot detection, classification, and response in the face of evolving threats.

Learn to classify bots into good, bad, and grey categories and apply the right management strategy for each.

Bots are used in both security and nonsecurity attacks. Identity and access management leaders must build a strong business case for a bot management capability or their organizations will incur avoidable losses due to account takeovers and also be unprepared to manage the risks introduced by customers using AI agents.

If AI is the next great computer interface, why are we still clicking on icons and navigating menus? Exploring the major hurdles standing between us and a true AI-native operating system.

We've gone from command lines to graphical interfaces. The next great leap in how we interact with computers won't be seen, it will be understood. AI is poised to become the ultimate translator between human intent and machine execution.

Exploring how AI can dramatically accelerate the process of turning complex academic research into functional code, with examples from anomaly detection to small LLMs.
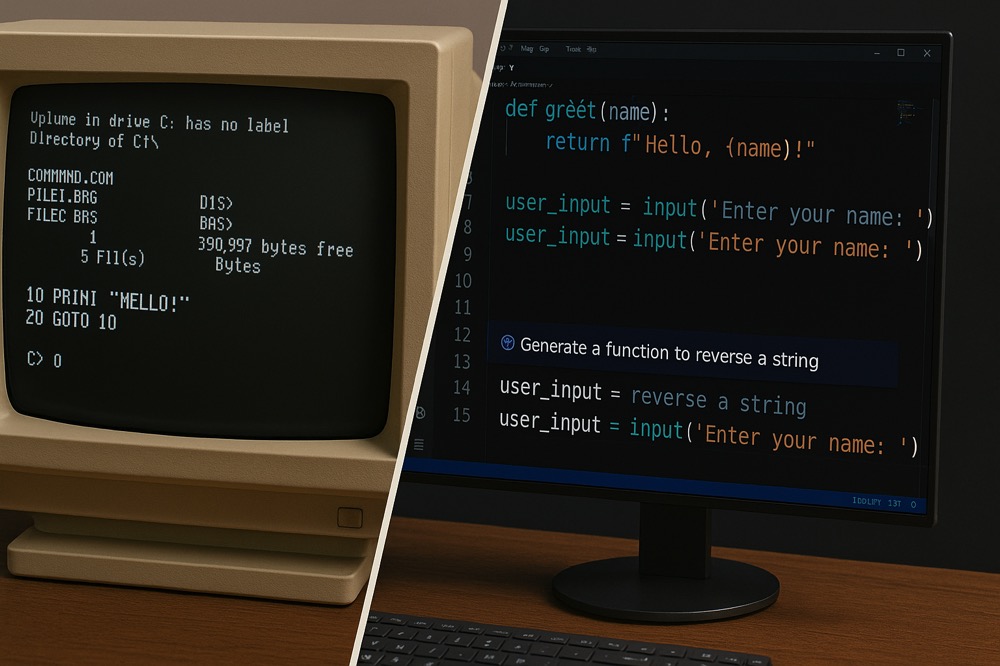
A personal journey through the evolution of programming, from the early days of DOS and BASIC to the current age of AI-assisted coding.

SMS pumping fraud cost businesses $6.7 billion in 2021. Learn how these sophisticated attacks work, which companies face the highest risk, and the most effective protection strategies.

The proliferation of residential proxy networks has undermined traditional IP-based security, enabling attackers to bypass protection measures while appearing as legitimate users.

AI agents with reasoning capabilities like DeepSeek are revolutionizing exploit development, marking the end of traditional security approaches based on static rules and patterns.

How AI agents are skewing marketing metrics and why traditional A/B testing needs to evolve for the age of autonomous digital interactions.

An exploration of how AI agents are reshaping API design principles and why we must evolve our approach to serve both machine and human consumers.
How Peakhour's contextual security aligns with Visa's data-driven risk management approach in the 2025-2028 Security Roadmap.

How open reasoning models transform automation from rigid scripts to autonomous agents, fundamentally changing our approach to security and digital interactions.

How residential proxy networks may have enabled DeepSeek to bypass AI platform protections, leading to Nvidia's historic market value loss

An analysis of how Peakhour's solutions help prevent enumeration attacks, aligning with Visa's Security Roadmap 2025-2028 priorities.

An analysis of Visa's Security Roadmap 2025-2028 and how Peakhour's solutions help Australian businesses meet these security objectives.

Understand the impact of bot traffic on A/B testing results and learn how to protect your optimization efforts

Learn how MTU fingerprinting reveals VPN usage, mobile connections, and network technologies through TCP handshake analysis. Discover practical SQL techniques for dynamic network intelligence.

Anti-detect browsers represent one of the most sophisticated threats facing modern web applications and APIs. Learn how these tools work, why they pose a significant threat to application security, and how modern security platforms can detect and mitigate their use.

Learn how distributed bot networks using residential IPs are evolving to evade traditional fraud detection

Comprehensive analysis of AI-powered cyber threats and how modern application security platforms defend against machine learning-driven attacks. Learn advanced defence strategies for the AI cybersecurity arms race.

Comprehensive guide to enterprise bot management for modern application security platforms. Learn how to protect applications and APIs from sophisticated bot threats including anti-detect browsers, credential stuffing, and automated attacks targeting DevOps environments.

An in-depth look at the growing threat of credential stuffing attacks on Australian businesses, including recent case studies, defense challenges, and practical recommendations.

Examine why current security solutions fail to detect and mitigate threats from residential proxies, and the need for comprehensive protection strategies.

Explore the complexities of residential proxy detection and its impact on organisational risk, with a focus on quantifying the threat and reframing security approaches.

Explore strategies to enhance web application security without compromising user experience, focusing on contextual security and adaptive authentication measures.

Explore how credential stuffing attacks and account takeovers affect business reputation and customer trust.

Our 2024 survey reveals Australian businesses are increasingly recognising and addressing account protection challenges, with a focus on combating credential stuffing attacks and the emerging threat of residential proxies.

Our 2024 survey reveals Australian businesses are increasingly recognising and addressing account protection challenges, with a focus on combating credential stuffing attacks and the emerging threat of residential proxies.

Multi-factor authentication alone cannot protect against sophisticated AI-powered attacks and residential proxy networks. Learn how modern application security platforms provide comprehensive account takeover prevention through multi-layered defence strategies.

An analysis of Peakhour's role in addressing key cloud security categories identified in recent industry analysis, demonstrating its comprehensive approach to modern cloud security challenges.

Comprehensive guide to breached credentials protection within modern application security platforms. Learn how to defend against credential stuffing attacks using advanced risk profiling and contextual security measures.

How advanced rate limiting protects modern applications and APIs from sophisticated threats including proxy networks, distributed attacks, and automated abuse in enterprise security environments.

Comprehensive guide to HTTP security headers for protecting web applications from client-side attacks. Learn essential browser security configurations for modern application security platforms and DevSecOps workflows.

Introducing SVCB and HTTPS records in DNS and their impact on web connectivity.
Understand CVSS by examining the Atlassian CVE-2023-22515 and CVE-2023-22518.

An in-depth exploration of EPSS, its data-driven approach to assessing cybersecurity threats, and how it complements CVSS.

Reviewing the CVSS an EPSS CVE scoring systems in light of the Atlassian Confluence-Aggedon

Explore the complexities of switching CDN providers amid industry consolidation and how Peakhour can assist in the transition

An exploration of Google Chrome's new "IP Protection" feature and a comparison with Apple's iCloud Private Relay.

An in-depth exploration of the JA4+ network fingerprinting method, its applications, and its role in cybersecurity.

An exploration of Google Chrome's new "IP Protection" feature, its promise of enhanced privacy.

ModSecurity's end-of-life marks a pivotal moment in application security evolution. Discover how modern Application Security Platforms are advancing beyond traditional WAF approaches to provide comprehensive protection for web applications and APIs at the edge.

The technicalities of the HTTP/2 Rapid Reset vulnerability and steps to fortify against DDoS threats.

A comprehensive breakdown of the HTTP/2 Rapid Reset flaw and guidance on bolstering defences against potential DDoS attacks.

A comprehensive look at OpenBullet, its capabilities, and the implications for cybersecurity in the face of its misuse.

Google Chrome is advancing towards making the web secure by default through HTTPS-First Mode.

Details the use of ZDNS, a high-performance DNS toolkit, to create a comprehensive Reverse DNS (rDNS) lookup database by scanning the entire internet, and how randomizing the IP space overcomes UDP timeout issues.

Analysis of the Microsoft 365 DDoS attack by Storm-1359 reveals critical lessons for enterprise application security platforms. Learn advanced Layer 7 DDoS protection strategies and rate limiting techniques for modern applications.

How can maximising website speed boost your company's revenue, especially during an impending economic recession?

What Apple's announcement of JPEG-XL support means for the web ecosystem.

Residential proxy malware, and its implications for traditional cybersecurity measures, emphasising the need for evolving threat detection and mitigation strategies.

Explore residential proxies within the context of the MITRE ATT&CK framework, highlighting the security implications and ethical considerations.

Comprehensive analysis of residential proxy threats and detection strategies for modern application security platforms. Learn how sophisticated threat actors use residential proxies to bypass traditional security measures.

Deep dive into Robust Random Cut Forest (RRCF) implementation for real-time anomaly detection in Application Security Platforms. Learn how advanced machine learning algorithms enhance threat detection and automated response capabilities.

An overview of consistent hashing with bounded loads, an advanced load balancing technique that ensures a more even distribution of keys across servers, preventing overload and improving system stability.
This article explores the use of Double Median Absolute Deviation (Double MAD) for anomaly detection in time series data, particularly in skewed or non-symmetric distributions.

A look at the limitations of Double MAD for anomaly detection, and a comparison with the Z-score method, to help you choose the right approach for your data.

Explains how to efficiently generate all IPv4 addresses in a random order using a Linear Congruential Generator (LCG), a memory-efficient method for tasks like security testing and network simulation.

An introduction to Locality Sensitive Hashing (LSH) and its application in load balancing, including consistent hashing and its use in CDNs and Google's Maglev for efficient server pool management.

Discusses strategies for scaling the Robust Random Cut Forest (RRCF) algorithm for large-scale anomaly detection, including using summary statistics, buffering input, and parallelisation.

Explores various thresholding techniques like Median Absolute Deviation (MAD), Min/Max, and Z-Score for interpreting Robust Random Cut Forest (RRCF) anomaly scores, crucial for classifying data points as normal or anomalous.

We bid farewell to JPEG-XL after its abrupt deprecation by Google, reinforcing the tech giant's domineering influence over the web and sparking a call for resilient alternatives.

Comprehensive guide to Layer 7 DDoS protection using strategic caching within application security platforms. Learn how intelligent caching strategies provide robust defence against sophisticated application-layer attacks.

Does TLS extension randomisation assist in hiding Chrome?

What is fingerprinting, and in particular TLS fingerprinting?

Image optimisation saves you bandwidth and designer effort while reduces page load time.

Comprehensive guide to IP threat intelligence for modern application security platforms. Learn how managed IP reputation lists and threat intelligence feeds protect applications from known malicious sources and emerging threats.

Origin shield is a CDN must have feature that increases your Cache Hit Rate by consolidating requests from POPs.

Peakhour clients are protected against CVF-2022-26134 Atlassian Confluence RCE

Cache keys allows the segmenting of the Peakhour.IO cache by elements of both the request and response, enabling effective and flexible caching of content.

Comprehensive guide to intelligent rate limiting for modern application security platforms. Learn how sophisticated rate limiting protects APIs and web applications from abuse, DDoS attacks, and automated threats whilst maintaining optimal user experience.

How can rate limiting protect your web application and the key items to consider when enabling.

Request collapsing - saving your origin by reducing concurrent requests and re-using responses for resources.

CDN-Cache-Control is a proposed new header to augment the venerable Cache-Control. Its aim is to make controlling caching easier as CDNs become ubiquitous.

Cache-Status is a proposed standard header to provide visibility into how caching providers interact and handle a request.

Comprehensive guide to enterprise bot management and advanced countermeasures for protecting applications against sophisticated malicious bot threats. Learn proven strategies for bot detection, mitigation, and automated defence systems.

Are Australian Magento stores prepared for the introduction of Core Web Vitals as a search signal? Read on to find out.
Comprehensive analysis of malicious bot threats targeting modern applications and APIs. Learn how enterprise bot management protects against automated attacks, credential stuffing, price scraping, and sophisticated bot-driven financial damage.
© PEAKHOUR.IO PTY LTD 2025 ABN 76 619 930 826 All rights reserved.