Automotive Cybersecurity for Connected Vehicles
Protecting the next generation of connected vehicles from API-driven threats, fraud, and abuse with Peakhour's unified security platform.
Secure Your Automotive PlatformAutomotive Industry Threat Protection
Connected Vehicle API Protection
Secure the APIs that power telematics, remote services, and vehicle-to-everything (V2X) communication. Protect against data theft and unauthorised commands.
Prevent Remote Vehicle Attacks
Stop malicious actors from exploiting vulnerabilities to remotely unlock, start, or control vehicles. Prevent theft and ensure driver safety.
Meet Regulatory Compliance
Address key cybersecurity regulations like UNECE R155 and ISO 21434. Demonstrate due diligence in protecting vehicle systems and data.
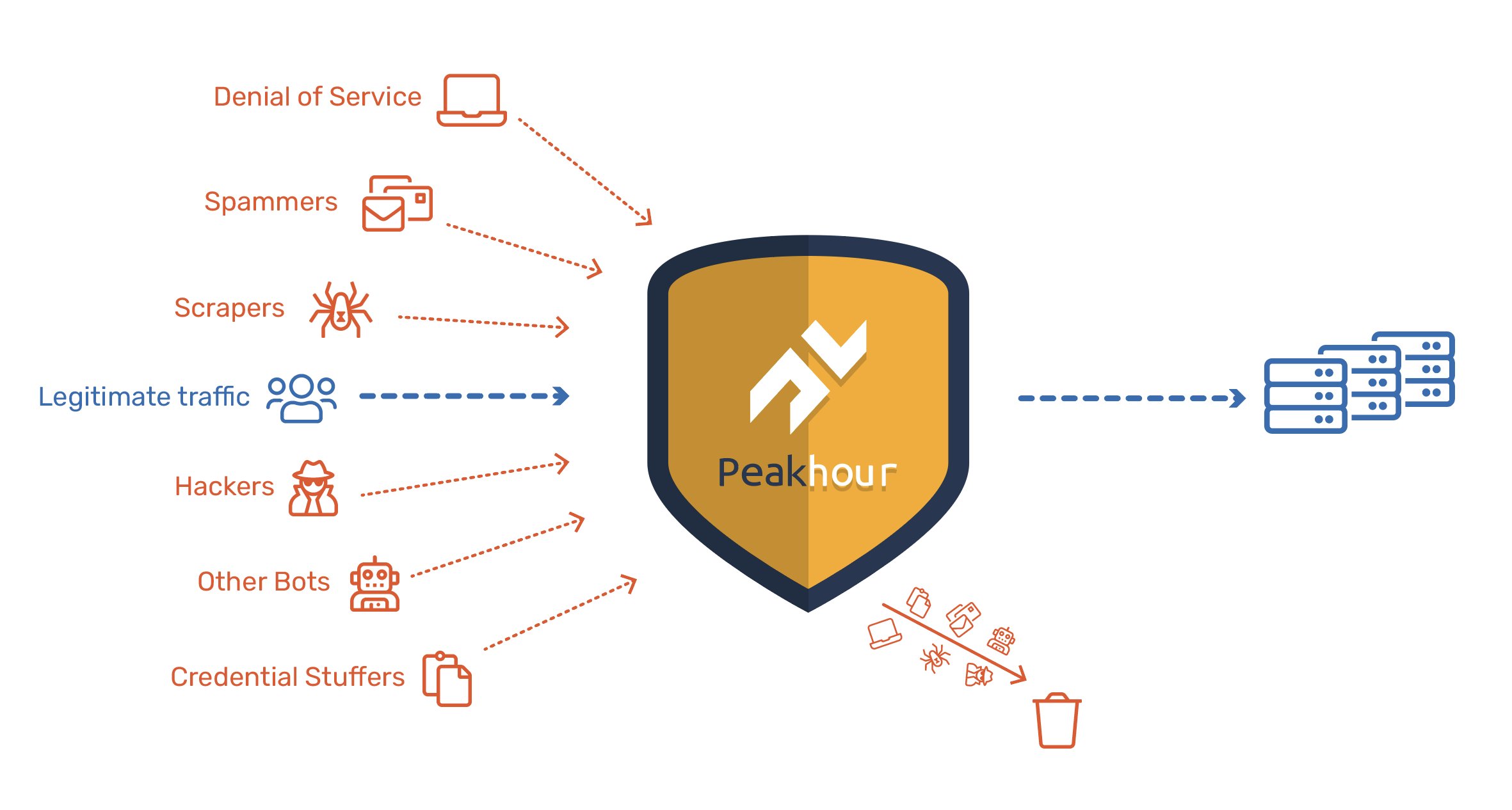
The Challenge of Automotive Cybersecurity
As vehicles become more connected, they expose a vast attack surface. APIs are the foundation of this connectivity, but also the primary vector for remote attacks, making robust API security essential.
Remote Attacks on Vehicles
Attackers can exploit APIs to steal vehicles, access personal data, or even control vehicle functions while in motion.
Complex Supply Chains
Vulnerabilities in software from numerous suppliers and up to 150 Electronic Control Units (ECUs) create significant risk.
Reputation and Liability
A single security incident can lead to significant financial liability, regulatory penalties, and irreparable damage to brand trust.
API Security for the Entire Vehicle Lifecycle
From manufacturing to on-road operation, APIs are critical. Peakhour provides a holistic approach to defending against API-related cybersecurity risks, covering the OWASP API Security Top 10 and beyond.
Our platform helps you:
- Protect Vehicle APIs: Secure APIs for telematics, infotainment, and remote keyless entry systems.
- Secure Dealer Portals: Prevent unauthorised access to internal systems and customer data.
- Stop Account Takeovers: Block credential stuffing attacks against customer and fleet management accounts.
- Defend Against DDoS: Mitigate Layer 7 DDoS attacks targeting connected vehicle services.
Compliance and Data Privacy
The automotive industry is subject to strict cybersecurity standards. Peakhour helps you meet these requirements and protect sensitive Personally Identifiable Information (PII).
Key compliance and privacy features:
- UNECE R155 & ISO 21434: Implement controls to meet international cybersecurity regulations for vehicles.
- Data Loss Prevention: Prevent the exposure of sensitive customer and vehicle data through APIs.
- PII Protection: Safeguard vehicle-related PII to prevent fraud and protect customer privacy.
- Audit and Reporting: Maintain comprehensive logs for security analysis and compliance audits.
Limitations of Traditional Defences
Many organisations believe a WAF or API gateway is sufficient. However, these traditional approaches often rely on easily evadable detection methods and lack the real-time ability to distinguish between legitimate and malicious API activity.
Attackers can leverage seemingly legitimate API calls to control vehicles or steal data. A modern, unified protection platform is required to defend against these sophisticated attacks.
Protect Your Connected Vehicles Today
Relevant information from our blog

Advanced Rate Limiting for API Security
How advanced rate limiting protects modern applications and APIs from sophisticated threats.
Read More
Residential Proxies, Friend or Foe?
This article explores the world of residential proxies, revealing the challenges and ethical questions they pose in our GeoIP-dependent digital landscape.
Read More
The Rise of OpenBullet: Automation Tool or Cybersecurity Threat?
A comprehensive look at OpenBullet, its capabilities, and the implications for cybersecurity in the face of its misuse.
Read More