Financial Services Security Platform
Protect your applications and APIs from fraud and abuse. Peakhour provides a comprehensive security platform for financial institutions to meet regulatory compliance and protect customer data.
Secure Your Financial PlatformFinancial Industry Threat Protection
Advanced Fraud Detection
Real-time fraud detection using machine learning to identify suspicious transactions, SMS pumping fraud, and account activities before financial loss occurs. Protect your customers and your reputation.
Account Takeover Prevention
Protect customer accounts from credential stuffing and brute-force attacks using residential proxies with advanced authentication security and breached credential detection.
Regulatory Compliance Support
Strengthen your compliance posture for APRA CPS 234, PCI DSS, and CDR requirements through comprehensive logging, audit trails, and security controls that help demonstrate regulatory adherence.
The Challenge of Financial Application Security
Banks, credit unions, and other financial services organisations are a prime target for attackers seeking monetary gain. Attacks against APIs and web applications can introduce significant risk to the entire business.
Infrastructure Under Strain
Volumetric attacks against APIs can cause infrastructure costs to skyrocket and impact performance for legitimate users.
Overwhelmed Fraud Teams
Fraud teams are overwhelmed by unauthorised fraudulent activity that affects business operations, brand, and customers.
Damaged Customer Trust
A slow or unavailable website, or a compromised account can drive customers away and damage your brand's reputation.
Regulatory Compliance & Data Protection
Financial institutions face stringent regulatory requirements for data protection, incident reporting, and customer privacy. Peakhour helps you meet these obligations with automated compliance monitoring and reporting capabilities.
Compliance features:
- APRA CPS 234: Meet Australian Prudential Regulation Authority cybersecurity standards.
- PCI DSS Level 1: Complete payment card industry data security standard compliance.
- CDR & Open Banking: Secure APIs for Consumer Data Right and Open Banking initiatives.
- Audit Logging: Comprehensive logging and audit trails for regulatory examinations.
- Incident Reporting: Automated regulatory incident reporting and breach notification.
- Data Sovereignty: Australian-owned and operated for data sovereignty requirements.
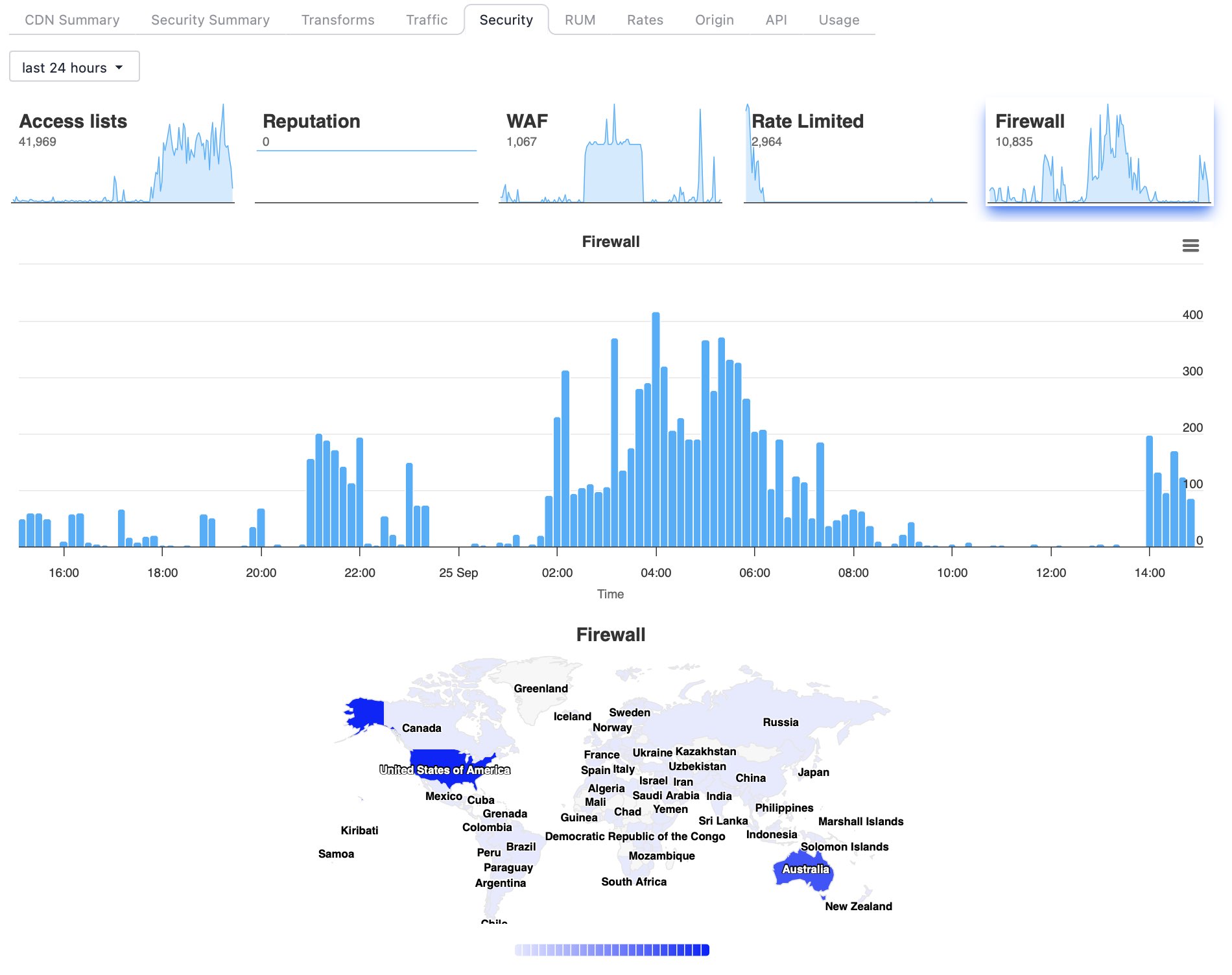
Financial Application Security
Protect critical financial applications including online banking, trading platforms, and payment processing systems. Peakhour provides comprehensive security controls designed for the unique threats faced by financial services.
Application security features:
- Transaction Security: Real-time transaction monitoring and anomaly detection.
- API Security: Secure REST, GraphQL, and WebSocket APIs with advanced threat protection.
- Mobile Banking Protection: Secure mobile applications from reverse engineering and fraud.
- Credential Stuffing Defence: Prevent account takeovers with breached credential scanning.
- Session Management: Secure session handling with contextual and multi-factor authentication.
- WAF/WAAP: Protect against OWASP Top 10 and zero-day vulnerabilities.
Limitations of Traditional Defences
Many organisations believe that a WAF or API gateway is sufficient to protect their APIs. However, these traditional approaches often rely on easily evadable detection methods and lack the real-time ability to distinguish between legitimate and malicious API activity.
Attackers can leverage seemingly legitimate transactions to steal data or commit fraud. A modern, unified protection platform is required to defend against these sophisticated attacks.
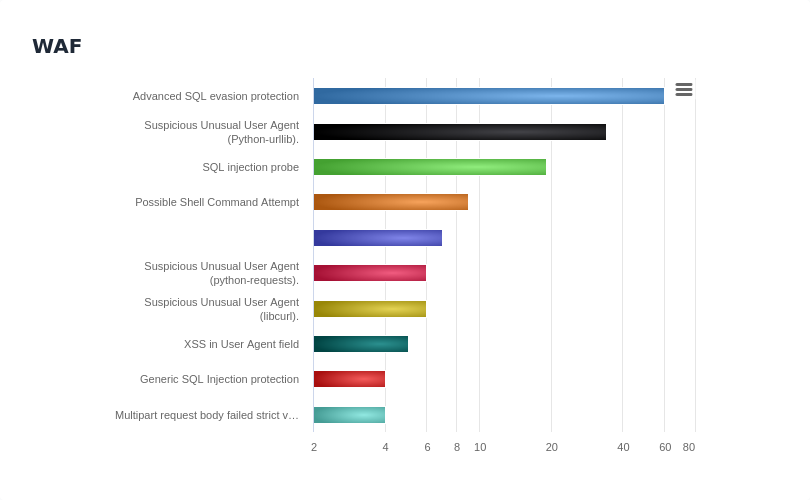
Protect Your Financial Institution Today
Relevant information from our blog
APRA Cybersecurity Guidelines: Application Security Requirements for Australian Financial Services
Comprehensive guide to APRA cybersecurity requirements for Australian financial institutions.
Read More
Breached Credentials Protection: Advanced Account Security for Application Platforms
Comprehensive guide to breached credentials protection within modern application security platforms. Learn how to defend against credential stuffing attacks using advanced risk profiling and contextual security measures.
Read More
The Iconic is the latest Account Takeover victim in the news
Popular Australian fashion website TheIconic recently suffered reputational damage from fraudsters placing orders after an account takeover. Learn how this happens and what you can do to stop it.
Read More