Online Dating Platform Security
Protect your users from romance scams, fake profiles, and account takeovers while ensuring a safe and seamless experience.
Secure Your PlatformKey Threats Facing Online Dating Apps
Fake Profile Creation
Malicious bots create fake accounts at scale to perpetrate romance scams, spam users, and damage your platform's credibility.
Account Takeover (ATO)
Attackers use credential stuffing and brute-force techniques to hijack legitimate user accounts, leading to identity theft and fraud.
Content & Profile Scraping
Automated bots scrape user profiles, personal information, and photos for use on other sites, violating user privacy and trust.
The Challenge of Securing Dating Platforms
Online dating services are built on trust. A single security incident can erode that trust, leading to user churn, brand damage, and financial loss. Protecting users from increasingly sophisticated automated attacks is a constant battle.
Sophisticated Scams
Romance scams cause significant financial and emotional distress, leading to reputational damage for your platform.
API Abuse
Attackers exploit APIs to automate malicious activities like profile creation, spamming, and data scraping at a massive scale.
Eroding User Trust
A proliferation of fake profiles and security incidents drives legitimate users away and harms your brand's reputation.
Stop Fake Account Creation
Peakhour's multi-layered defence stops bots at the source. By combining IP intelligence, sophisticated fingerprinting, and behavioural analysis, we can distinguish between human users and malicious bots with unparalleled accuracy.
Our Bot Management and Residential Proxy Detection solutions work together to block automated sign-ups, even from attackers trying to hide behind legitimate-looking IP addresses.
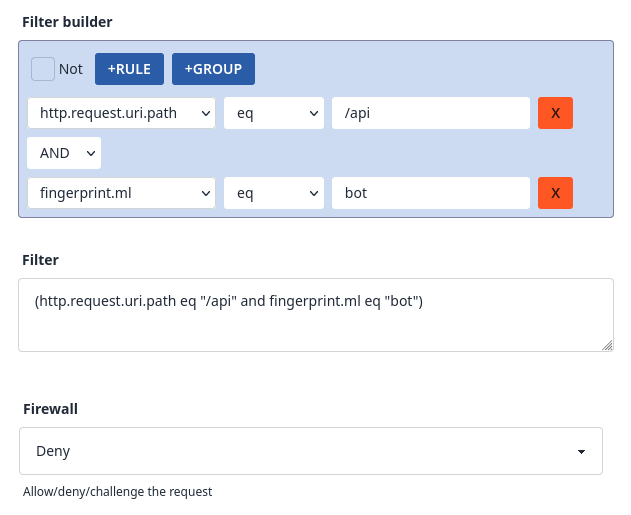
Prevent Account Takeover
Protect your users' accounts from unauthorised access. Peakhour's Breached Credential Scanning checks login attempts against a massive database of compromised credentials, stopping attackers in their tracks.
Combined with our advanced bot protection, we can effectively mitigate credential stuffing attacks, safeguarding user accounts and preventing fraud before it happens.

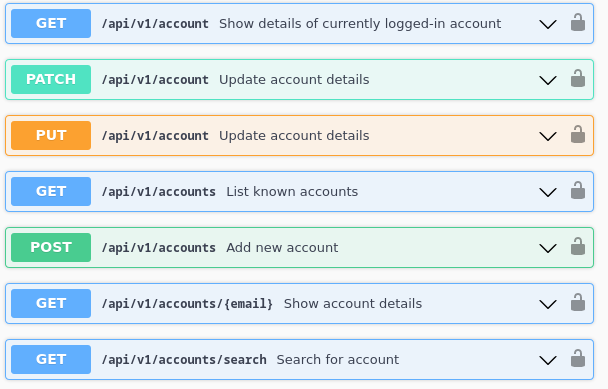
Protect Your APIs from Abuse
Your APIs are the backbone of your application, but they are also a primary target for attackers. Peakhour's API Security solution provides comprehensive protection against a wide range of threats.
With our Web Application Firewall (WAF) and Advanced Rate Limiting, you can enforce strict access controls, prevent data scraping, and stop denial-of-service attacks targeting your API endpoints.
Build a Safer Dating Community

Relevant information from our blog

Bad Bot Countermeasures
Bad bots can significantly impact your website and are hard to detect. Here we detail best practice on how to combat the growing threat from bad bots.
Read More
Residential Proxies, Friend or Foe?
This article explores the world of residential proxies, revealing the challenges and ethical questions they pose in our GeoIP-dependent digital landscape.
Read More
Breached Credentials Protection: Advanced Account Security for Application Platforms
Comprehensive guide to breached credentials protection within modern application security platforms. Learn how to defend against credential stuffing attacks using advanced risk profiling and contextual security measures.
Read More