DDoS Protection
Peakhour's Anycast network distributes requests across our global network. Combined with our WAF, Anomaly Detection, Bot Management, and Advanced Rate Limiting features you get Layer 7 protection that works.
Start Your Free TrialAdvanced Layer 7 DDoS Protection
Protect Your Revenue
With our expertise centred on Layer 7, Peakhour's DDoS protection is designed to meticulously safeguard your applications, websites, and web APIs from targeted attacks that could take your business offline and damage customer trust.
Dynamic Adaptation
As cyber threats evolve, so does our defence. Our DDoS protection system adapts to changing attack patterns, ensuring your business continuity without any performance compromise.
Guaranteed Service Availability
Onboard seamlessly with Peakhour's DDoS protection. Our user-friendly setup ensures uninterrupted operation, maintaining business continuity and reducing the operational overhead of emergency response.
Specialised Layer 7 Security
Peakhour's DDoS protection specialises in Layer 7 security, uniquely focusing on the application layer to shield your digital assets.
-
Mitigation for HTTP(S) GET and POST request floods
-
Protection against SlowLoris and other advanced Layer 7 threats
-
Robust defence for intricate attack patterns
-
Real-time threat detection and automatic mitigation
-
Business continuity assurance with guaranteed uptime

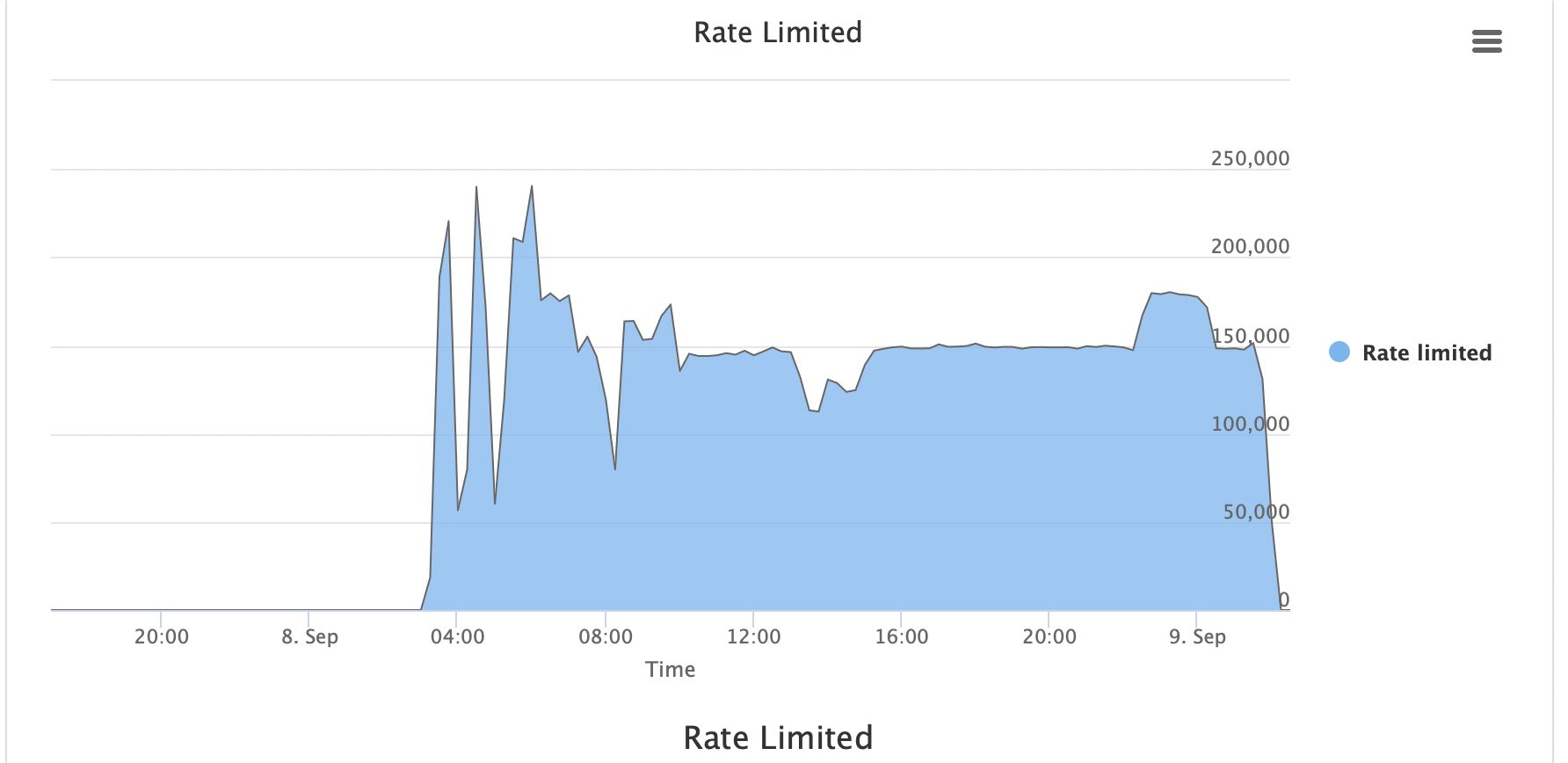
Advanced Rate Limiting
Peakhour's Advanced Rate Limiting allows you to count requests on connecting client characteristics, network, country, headers and more, rather than traditional IP-based counting. Easily set up layers of protection that catch distributed attacks regardless of the sophistication.
Our intelligent rate limiting adapts to attack patterns and provides granular control over traffic flow, ensuring legitimate users maintain access while malicious traffic is blocked.
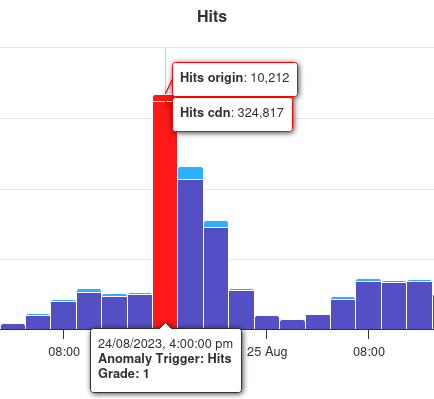
Anomaly Detection
Exclusively focusing on Layer 7, Peakhour's system can spot traffic anomalies in seconds, and can surgically mitigate the most sophisticated and harmful attacks targeting your applications and services.
Our machine learning algorithms continuously analyse traffic patterns to identify and respond to emerging threats before they impact your business operations.
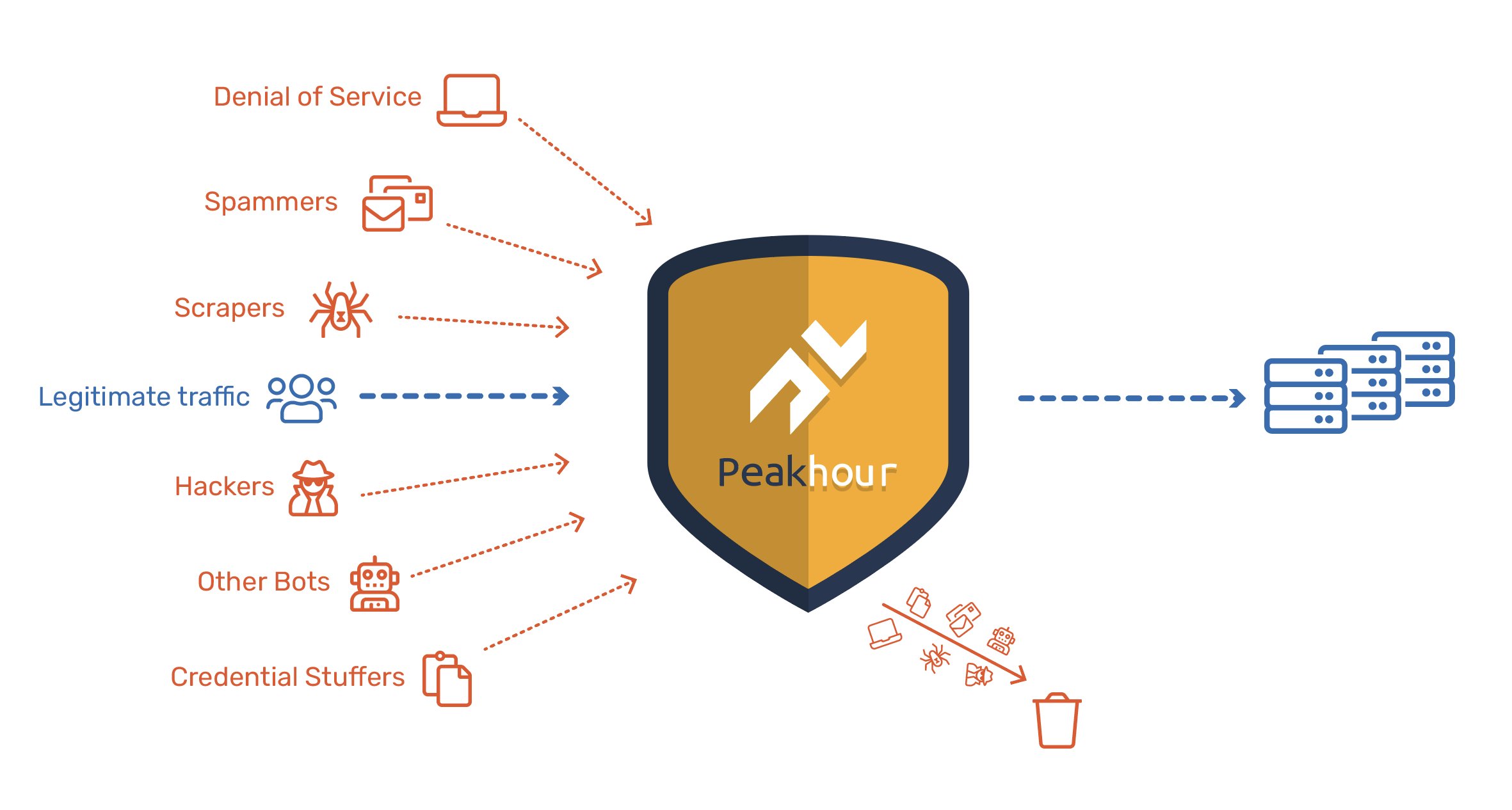
Comprehensive Security and Bot Management
Our massive database of IP threat intelligence and multi-layered security and bot management means emerging threats and attacks are stopped before they reach your infrastructure.
Advanced bot detection, behavioural analysis, and threat intelligence combine to provide unparalleled protection against automated attacks and malicious traffic.
Success Stories
Discover how leading organizations have transformed their cybersecurity posture and achieved measurable results with Peakhour's advanced protection platform.

COVID-19 Traffic Surge Success
How Australia's #1 online kitchenware retailer thrived during COVID-19's unprecedented traffic surge and achieved 150% revenue growth with Peakhour's performance solutions.

Fintech Hub Enterprise Security
How Australia's leading fintech hub secured hundreds of startups with enterprise-grade application security, zero-day vulnerability protection, and comprehensive threat management.
Explore Our DDoS Protection Platform
Protect Your Applications from DDoS Attacks

Relevant information from our blog

Layer 7 DoS attacks and Full Page Caching
Discover how Full Page Caching can help mitigate layer 7 DoS attacks.
Read More
Understanding the HTTP/2 Rapid Reset Attack: What It Means and How to Stay Protected
A comprehensive breakdown of the HTTP/2 Rapid Reset flaw and guidance on bolstering defences against potential DDoS attacks.
Read More
HTTP/2 Rapid Reset Attack Deepdive
The technicalities of the HTTP/2 Rapid Reset vulnerability and steps to fortify against DDoS threats.
Read More