Web Application & API Protection (WAAP)
Enterprise-grade security platform protecting web applications and APIs against OWASP Top 10 vulnerabilities, zero-day exploits, and sophisticated attacks with real-time threat detection designed for DevSecOps teams.
Start Your Free Trial91%
detection rate
4
Layers of protection
Complete
Works with all providers
Web Application Security Challenges
Modern web applications face numerous security threats. Our WAF addresses these challenges head-on.
Evolving Threats
Cyber threats change rapidly, requiring constant vigilance and updates.
Complex Attacks
Sophisticated attacks combine multiple vectors, making detection difficult.
Data Protection
Sensitive data needs protection from breaches and unauthorised access.
Modern API Protection
Next-Generation WAF
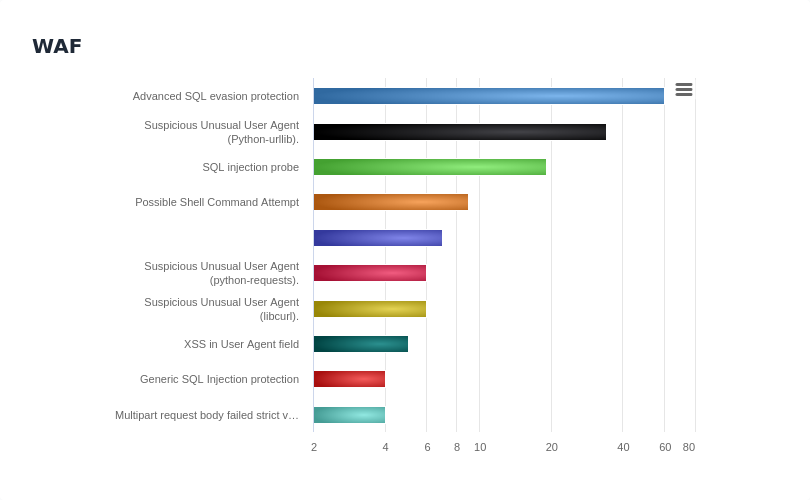
Peakhour WAF Solutions
Our WAF provides comprehensive protection for your web applications.
-
Bot Mitigation
We identify and stop malicious bots from performing harmful actions with our advanced mitigation features.
-
IP Intelligence
We analyse the geographical origin, reputation, and behaviour of incoming IPs to identify threats and secure your network.
Key WAF Features
Real-Time Threat Detection
Our WAF identifies and blocks threats as they occur, while minimising false positives to reduce manual reviews for your team.
Custom Rulesets
Create and deploy custom rulesets tailored to your specific security needs and application requirements.
Machine Learning
Our WAF uses advanced machine learning algorithms to adapt to new threats and improve detection over time.
Success Stories
Discover how leading organizations have transformed their cybersecurity posture and achieved measurable results with Peakhour's advanced protection platform.

Scaling with Performance
How Australia's innovative commercial law firm scaled from a two-person startup to 150+ employees whilst becoming the country's #1 online legal service provider.

Fintech Hub Enterprise Security
How Australia's leading fintech hub secured hundreds of startups with enterprise-grade application security, zero-day vulnerability protection, and comprehensive threat management.
Peakhour's WAF has significantly improved our web application security.
Evan Tait Styles, CTO
Explore Our Security Solutions
Protect Your Web Applications Today
Relevant information from our blog

Protecting the browser, an HTTP security header overview
Client side attacks on your website can have devastating impact on business credibility. Learn how to protect your clients with these HTTP Headers.
Read More
Layer 7 DoS attacks and Full Page Caching
Discover how Full Page Caching can help mitigate layer 7 DoS attacks.
Read More
The Rise of OpenBullet: Automation Tool or Cybersecurity Threat?
A comprehensive look at OpenBullet, its capabilities, and the implications for cybersecurity in the face of its misuse.
Read More
