Enforce Zero Trust Access for Corporate and SaaS Applications
Peakhour's Zero Trust Access brings a consistent login experience to every corporate application, evaluating every request for user identity and device context.
Secure Your ApplicationsThe Problem with Traditional Network Security
Using IP, VPN, and location-based controls for your business tools increases your attack surface, limits visibility, and creates a poor user experience.
Increased Attack Surface
Legacy VPNs expose your entire network, making it vulnerable to attack once a user is connected, potentially leading to devastating data breaches and operational disruption.
Limited Visibility
Lack of granular logging and context-aware policies makes it difficult to track access and respond to threats effectively, increasing compliance risks and audit failures.
Poor User Experience
VPNs are often slow and cumbersome, creating friction for users that reduces productivity and increases IT support costs, especially for remote workers and contractors.
Peakhour's Zero Trust Approach
Peakhour's Zero Trust Access replaces legacy corporate VPNs with our global network. Instead of backhauling traffic, users securely access internal applications from anywhere, while you maintain granular control and visibility.
-
Protect Any Web Application
Peakhour is identity and origin agnostic, allowing you to protect any web application whether it's SaaS, in the cloud, or on-premises, reducing IT complexity and operational overhead.
-
Context-Aware Access Policies
Control access to applications by checking for identity alongside other relevant contextual attributes, including location, device type, and MFA method, ensuring compliance and reducing security incident risk.
-
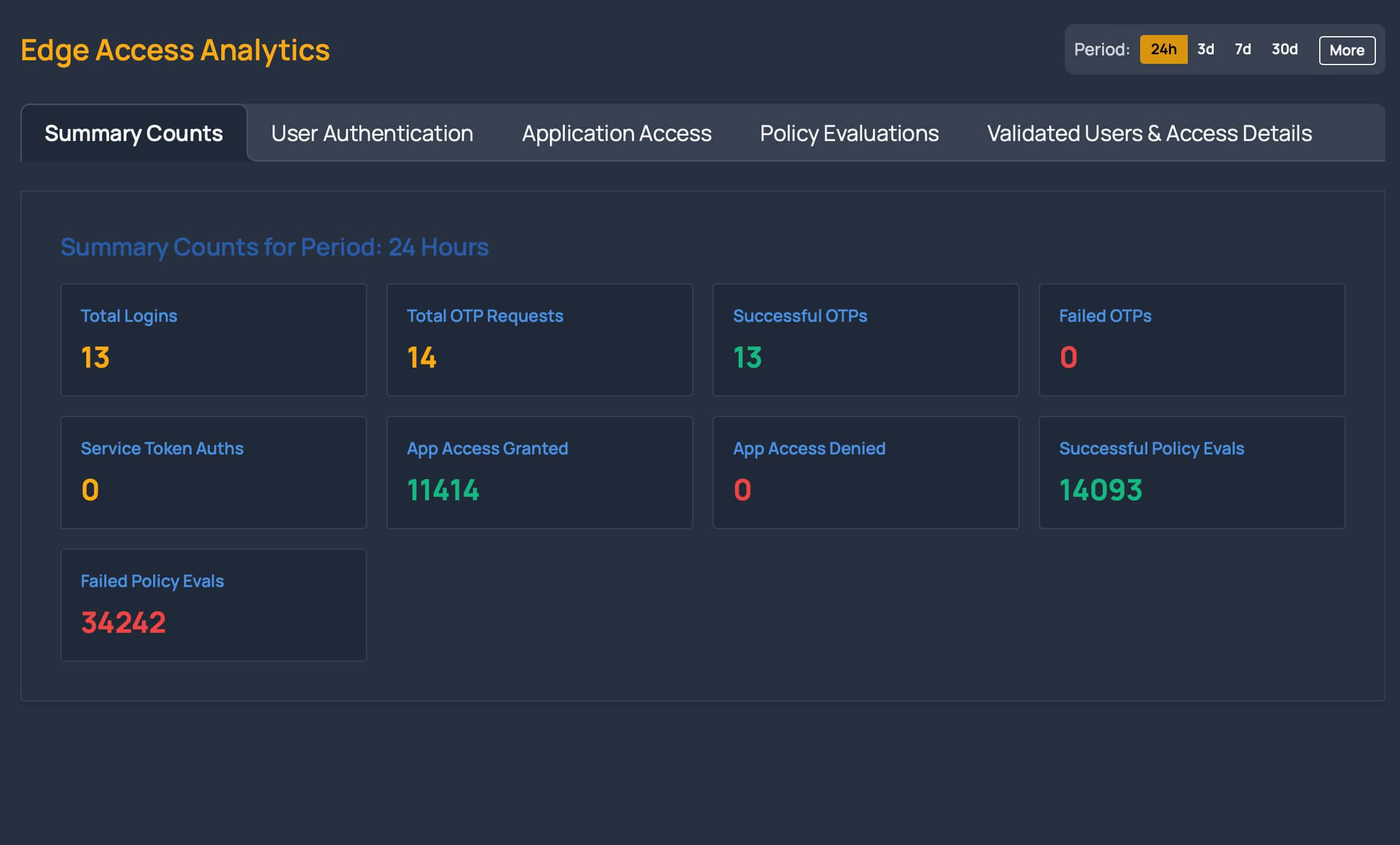
Log Every Request
Log any request made in your protected applications - not just login and log out. Aggregate activity logs in Peakhour, or export them to your SIEM provider, enabling faster threat response and simplifying compliance audits.
Granular Control for Modern Teams
Peakhour's Zero Trust Access provides the flexibility to secure your applications without compromising user experience.
-
Per-Application Policies: Configure different access rules for individual applications.
-
Contextual Rules: Build rules based on identity, device posture, location, IP range, and more.
-
Multi-Factor Authentication: Enforce MFA to add a critical layer of security to user logins.
-
Detailed Audit Logs: Gain visibility into every request to your applications, not just logins, for comprehensive security monitoring.
We needed a way to control access to specific critical resources without the risk and overhead of a private corporate network. Peakhour's Zero Trust Access aligns with how and where our team works, while helping us embrace a Zero Trust security model, where every request to every app is evaluated for user identity - and no VPN is required.
Michael Irwin, Senior Director, Technology Operations and Cybersecurity
Explore Our Security Platform
Application Security
Protect your web applications and APIs with our integrated WAAP.
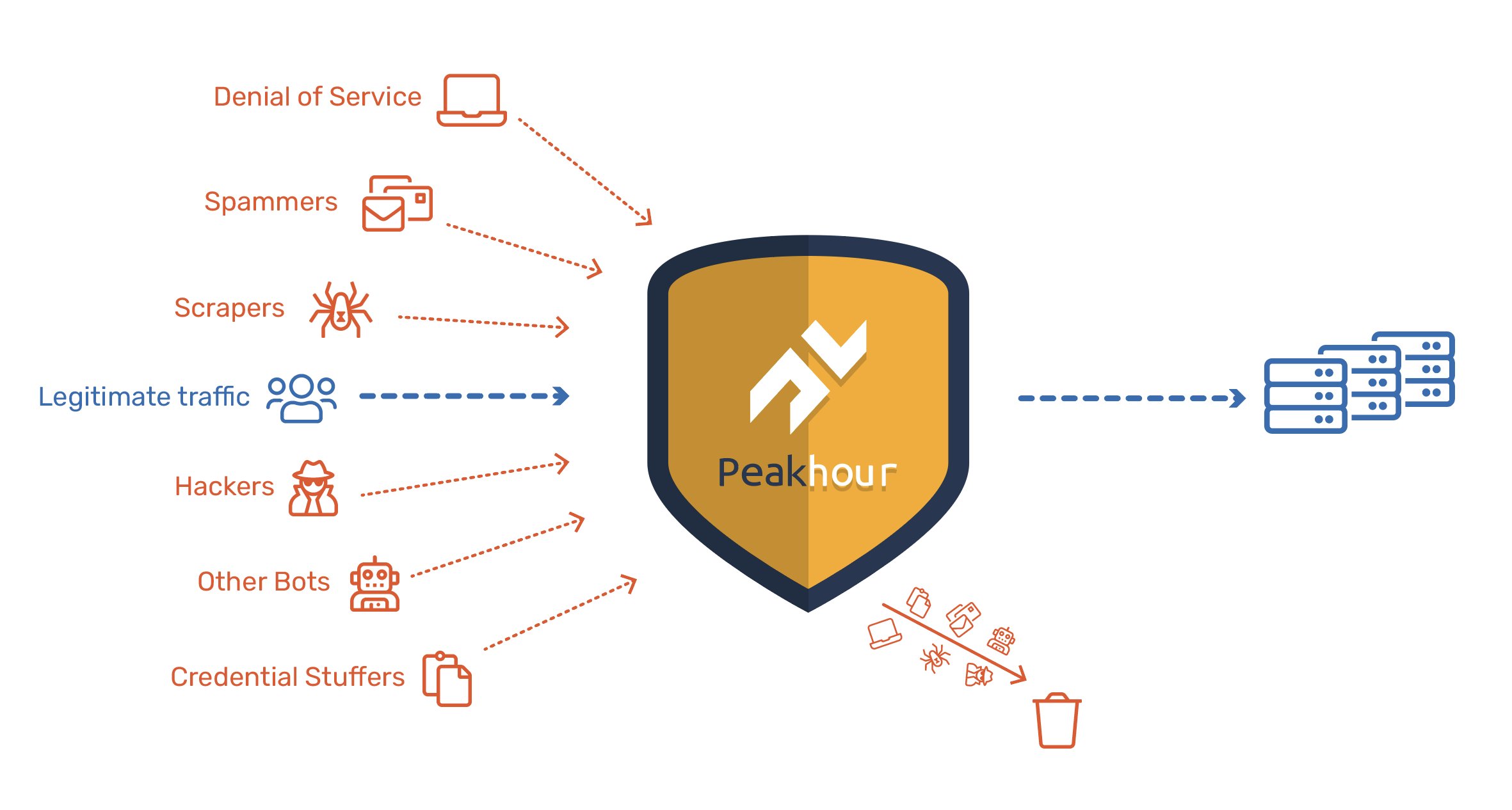
DDoS Mitigation
Maintain service availability during volumetric and application-layer attacks.
Bot Management
Identify and control automated traffic to protect your applications and users.
Replace Your VPN with a Modern Zero Trust Solution
Relevant information from our blog

ModSecurity’s End-of-Life: Implications for Peakhour and Customers
ModSecurity's end-of-life marks a pivotal moment in application security evolution. Discover how modern Application Security Platforms are advancing beyond traditional WAF approaches.
Read More
APRA Cybersecurity Guidelines: Application Security Requirements for Australian Financial Services
Comprehensive guide to APRA cybersecurity requirements for Australian financial institutions.
Read More
HTTP Security Headers: Essential Browser Protection for Web Application Security
Comprehensive guide to HTTP security headers for protecting web applications from client-side attacks.
Read More
