Advanced Rate Limiting
Protect your applications and APIs with precision and control against malicious traffic, without affecting legitimate users.
Get StartedAdvanced Rate Limiting Capabilities
Protect Revenue & Ad Spend
Count requests using keys like headers, ASN, country, IP, and fingerprints. Stop malicious traffic that wastes marketing budgets and threatens revenue streams without blocking real customers.
Granular Control
Set filters and thresholds to match your business logic. Maintain protection against new threats with custom rules for flexible security.
Reduce Operational Costs
Get full protection without hidden costs. Avoid surprise expenses from traffic spikes and attacks while reducing server load and operational overhead with no limits on traffic protection.
The Challenge of Modern Attack Techniques
Websites and APIs face threats from bots, scrapers, and malicious users. Traditional IP-based rate limiting falls short against distributed attacks using residential proxies.
Distributed Attacks
Attackers use distributed networks and residential IPs to bypass traditional rate limits.
Application Layer Attacks
Layer 7 DDoS and brute-force attacks can overwhelm your application resources.
API and Content Scraping
Automated tools scrape APIs and content, impacting performance and business intelligence.
Fine Targeting with Rules
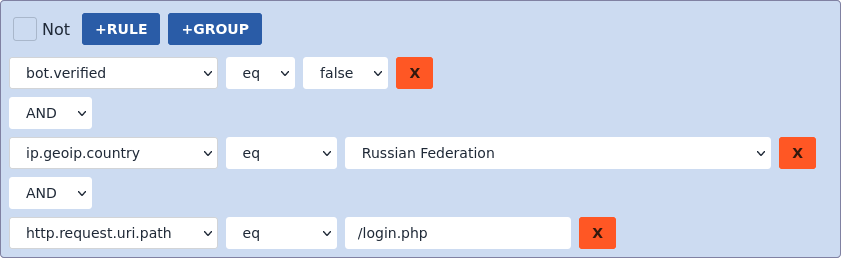
Configurable Request Thresholds
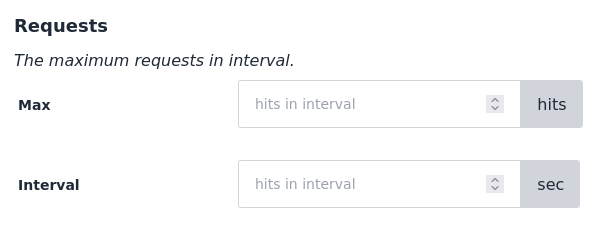
Customisable Keys
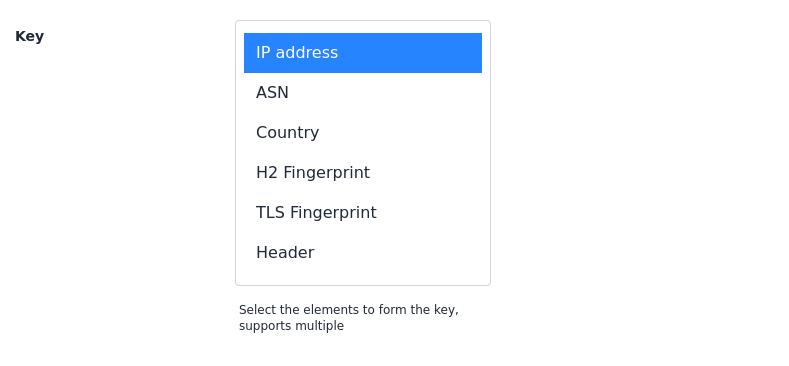
Advanced Features
Adaptive Thresholds
Automatically adjust rate limits based on traffic patterns and anomaly detection.
Real-time Analytics
Monitor traffic patterns and rate limit triggers with detailed, real-time dashboards.
Instant Rule Deployment
Apply new rate limiting rules instantly across our global network without delay.
Success Stories
Discover how leading organizations have transformed their cybersecurity posture and achieved measurable results with Peakhour's advanced protection platform.

Fintech Hub Enterprise Security
How Australia's leading fintech hub secured hundreds of startups with enterprise-grade application security, zero-day vulnerability protection, and comprehensive threat management.

Government Security Compliance & Bot Management
How Australia's National Gallery achieved government security compliance with advanced bot management, DDoS protection, and content scraping controls whilst improving digital visitor experience.
Peakhour's Advanced Rate Limiting has transformed our API security. We've seen a 99% reduction in malicious traffic while maintaining seamless access for our legitimate users.
Josh Sinclair, Head of Product
Explore Related Solutions
Application Security Platform
Discover our holistic approach to application and API security.
Bot Management
Detect and mitigate bot traffic while allowing legitimate users and good bots.
DDoS Mitigation
Protect your infrastructure from volumetric and application layer DDoS attacks.
Secure Your Application Today
Relevant information from our blog

Advanced Rate Limiting for API Security: Protecting Applications from Modern Threats
How advanced rate limiting protects modern applications and APIs from sophisticated threats.
Read More
Rate limiting - How it works
How can rate limiting protect your web application and the key items to consider when enabling.
Read More
Enterprise DDoS Protection: Lessons from Microsoft 365 Attack for Application Security
Analysis of the Microsoft 365 DDoS attack reveals critical lessons for enterprise application security platforms.
Read More