
Agentic AI vs. Your API
Understand the shift from scripted bots to reasoning AI agents and how to adapt your security strategy for this new reality.

Understand the shift from scripted bots to reasoning AI agents and how to adapt your security strategy for this new reality.

Discover why traditional IP-based rate limiting is obsolete and how advanced techniques provide robust protection against modern distributed attacks.

With nearly half of all internet traffic being automated, a robust bot management strategy is essential. This article explores the key considerations for effective bot detection, classification, and response in the face of evolving threats.

Learn to classify bots into good, bad, and grey categories and apply the right management strategy for each.

Bots are used in both security and nonsecurity attacks. Identity and access management leaders must build a strong business case for a bot management capability or their organizations will incur avoidable losses due to account takeovers and also be unprepared to manage the risks introduced by customers using AI agents.

AI agents with reasoning capabilities like DeepSeek are revolutionizing exploit development, marking the end of traditional security approaches based on static rules and patterns.

An exploration of how AI agents are reshaping API design principles and why we must evolve our approach to serve both machine and human consumers.
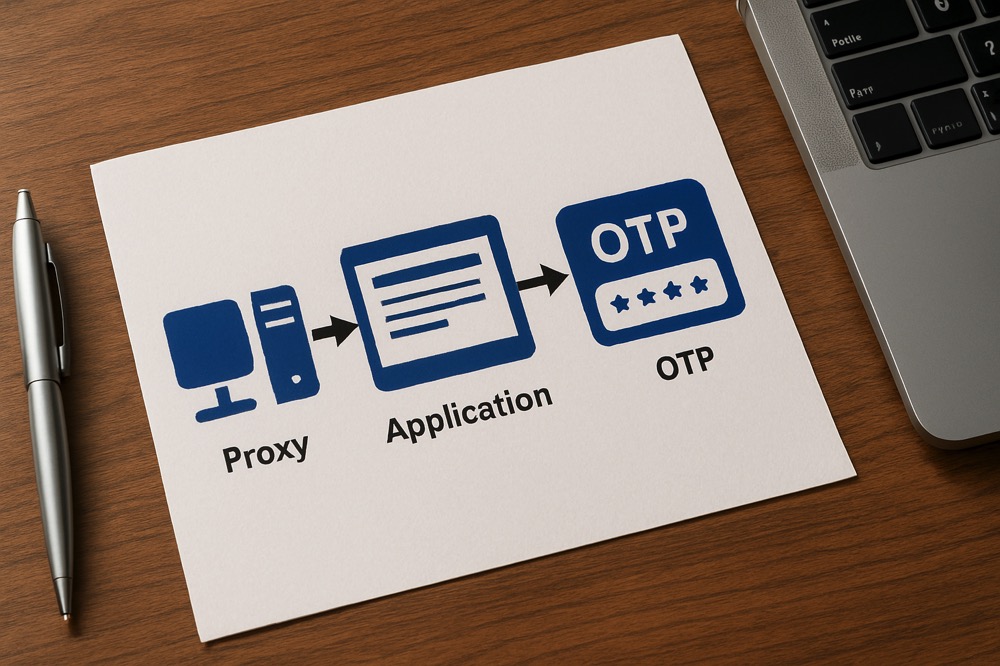
How Peakhour's contextual security aligns with Visa's data-driven risk management approach in the 2025-2028 Security Roadmap.

How residential proxy networks may have enabled DeepSeek to bypass AI platform protections, leading to Nvidia's historic market value loss

An analysis of how Peakhour's solutions help prevent enumeration attacks, aligning with Visa's Security Roadmap 2025-2028 priorities.

Comprehensive guide to enterprise bot management for modern application security platforms. Learn how to protect applications and APIs from sophisticated bot threats including anti-detect browsers, credential stuffing, and automated attacks targeting DevOps environments.

Examine why current security solutions fail to detect and mitigate threats from residential proxies, and the need for comprehensive protection strategies.

Explore strategies to enhance web application security without compromising user experience, focusing on contextual security and adaptive authentication measures.

Our 2024 survey reveals Australian businesses are increasingly recognising and addressing account protection challenges, with a focus on combating credential stuffing attacks and the emerging threat of residential proxies.

Our 2024 survey reveals Australian businesses are increasingly recognising and addressing account protection challenges, with a focus on combating credential stuffing attacks and the emerging threat of residential proxies.

Multi-factor authentication alone cannot protect against sophisticated AI-powered attacks and residential proxy networks. Learn how modern application security platforms provide comprehensive account takeover prevention through multi-layered defence strategies.

An analysis of Peakhour's role in addressing key cloud security categories identified in recent industry analysis, demonstrating its comprehensive approach to modern cloud security challenges.

Comprehensive guide to breached credentials protection within modern application security platforms. Learn how to defend against credential stuffing attacks using advanced risk profiling and contextual security measures.

How advanced rate limiting protects modern applications and APIs from sophisticated threats including proxy networks, distributed attacks, and automated abuse in enterprise security environments.

Comprehensive guide to HTTP security headers for protecting web applications from client-side attacks. Learn essential browser security configurations for modern application security platforms and DevSecOps workflows.

An exploration of Google Chrome's new "IP Protection" feature and a comparison with Apple's iCloud Private Relay.

An exploration of Google Chrome's new "IP Protection" feature, its promise of enhanced privacy.

ModSecurity's end-of-life marks a pivotal moment in application security evolution. Discover how modern Application Security Platforms are advancing beyond traditional WAF approaches to provide comprehensive protection for web applications and APIs at the edge.

A comprehensive breakdown of the HTTP/2 Rapid Reset flaw and guidance on bolstering defences against potential DDoS attacks.

Comprehensive analysis of security challenges in headless commerce and Single Page Applications. Learn how to protect modern e-commerce APIs and microservices architectures from scraping, fraud, and automated attacks.

Analysis of the Microsoft 365 DDoS attack by Storm-1359 reveals critical lessons for enterprise application security platforms. Learn advanced Layer 7 DDoS protection strategies and rate limiting techniques for modern applications.

Does TLS extension randomisation assist in hiding Chrome?

Comprehensive guide to IP threat intelligence for modern application security platforms. Learn how managed IP reputation lists and threat intelligence feeds protect applications from known malicious sources and emerging threats.

Peakhour clients are protected against CVF-2022-26134 Atlassian Confluence RCE

Comprehensive guide to intelligent rate limiting for modern application security platforms. Learn how sophisticated rate limiting protects APIs and web applications from abuse, DDoS attacks, and automated threats whilst maintaining optimal user experience.

How can rate limiting protect your web application and the key items to consider when enabling.

Comprehensive guide to enterprise bot management and advanced countermeasures for protecting applications against sophisticated malicious bot threats. Learn proven strategies for bot detection, mitigation, and automated defence systems.
Comprehensive analysis of malicious bot threats targeting modern applications and APIs. Learn how enterprise bot management protects against automated attacks, credential stuffing, price scraping, and sophisticated bot-driven financial damage.
© PEAKHOUR.IO PTY LTD 2025 ABN 76 619 930 826 All rights reserved.